Key Skills Developed From This Project
- How to set up networks in VMware Workstation 17 Pro.
- Disable Microsoft Defender and establish a command & control (C2) server on a victim.
- Monitor a Windows endpoint for malicious processes with LimaCharlie and Sysmon.
- Craft a Detection & Response (D&R) rule for certain events to detect and block attacks.
- Control a sever with SSH.
- Analyze telemetry to identify which processes are potentially malicious.
- Scan for malicious files by YARA signature.
- Use VirusTotal to check if a file hash is associated with previously identified malware, and why malware may not be identified by VirusTotal.
- Analyze a detection to see if it’s likely a false positive.
- Limit the rate of false positives from the D&R rules in the EDR.
So you want to be a SOC Analyst?
I completed this project by following the guidance of Eric Capuano in his blog posts titled “So you want to be a SOC Analyst?”
https://blog.ecapuano.com/p/so-you-want-to-be-a-soc-analyst-intro?utm_campaign=post&utm_medium=web
I’m very appreciative that he made such a great resource to help people like myself learn practical skills in preparation to be a SOC analyst.
One of the aspects of this project that made it more rewarding was the many problems I encountered when following the steps. It did not simply work every time and I had to tinker with many things not mentioned in the blog post. It lead me down hours of researching solutions and getting a broader understanding of the tools and concepts used in this project. Even when reading through the comments of others who had completed this homelab, I could not find anyone else who reported the same problems I had. I think it was valuable to get experience troubleshooting with systems I was not familiar with, and having to learn more about a tool or software as a whole to even be able to diagnose the potential problem.
I’m primarily going to focus on discussing what I learned, rather than showing step by step every single thing I did in this project. If you’re curious to see everything step by step in detail then you can visit Eric’s blogpost linked above. What I learned is far more important than what I did.
Getting used to VMware
Before I could start this project, I needed to do a bit of research and practice with VMware. I had used other hypervisors before like Proxmox, Qemu, QubesOS, and Virtual Box, but VMware had a few differences which I wanted to get comfortable with before learning how to use the other new tools in this project. I purchased the license for VMware Workstation 17 Pro, as I’m sure I will continue to use it throughout my career, and VMware products are commonly used at an enterprise level. I’ve even started using it for my personal use to increase privacy and security. It certainly performs better than Virtual Box.
Problems Running the Command and Control Server
One of the problems I encountered was Windows updating every time I closed down the VM to step away from the project. The update made it so my malicious file would be deleted, even with Microsoft Defender still being disabled. This is why I am glad I took a snapshot of the Windows VM right after the C2 file was downloaded. It meant that all I had to do was load that snapshot the next time I wanted to continue messing around with it. For this project, It didn’t really matter because all of the data I needed was in the logs on LimaCharlie, and nothing was being saved to the Windows VM.
What I Learned About LimaCharlie Logs
One very useful thing I learned about monitoring a Windows endpoint is to first look for unsigned files. The malicious C2 .exe file was the only file on the whole system which was unsigned. That is a huge red flag. LimaCharlie makes it easy to see if a file is signed by putting a checkmark icon on it.
The attack I performed on the Windows VM was a dump of the lsass.exe process from memory with the procdump command. this gave me an opportunity to see what a “SENSITIVE_PROCESS_ACCESS” event looks like in LimaCharlie. In the case of a dump of the lsass.exe process, there is a good probability that this is an indicator of compromise because it is not common for this to happen in a healthy system. For this reason we want to make a D&R rule for this event.
Using Virus Total
One nice feature of LimaCharlie is the ability to easily look up a file you found in your endpoint to see if it shows up as a known malicious file in Virus Total. The C2 file I used was generated by Sliver, so it did not show up. This is an important lesson in why you can’t just assume a file is not malicious if it doesn’t show up in Virus Total.
Just to get a bit of experience with Virus Total outside of LimaCharlie, I took the file’s hash and ran it through Virus Total without using LimaCharlie. I got the same result as I expected. I just wanted to get practice with checking a file’s hash in Virus Total in case I work in an environment with tools that don’t have an integrated feature to search Virus Total directly from the logs.
Making D&R Rules in LimaCharlie
Detection & Response (D&R) rules are great for making an automated response occur for a certain event. For this example I want the D&R rule to cause an alert if there is a log that is for a “SENSITIVE_PROCESS_ACCESS” event which has a process that ends with lsass.exe. This is a very simple rule just to get started learning the basics. For the response section, I just want this rule to make an alert called “LSASS access”
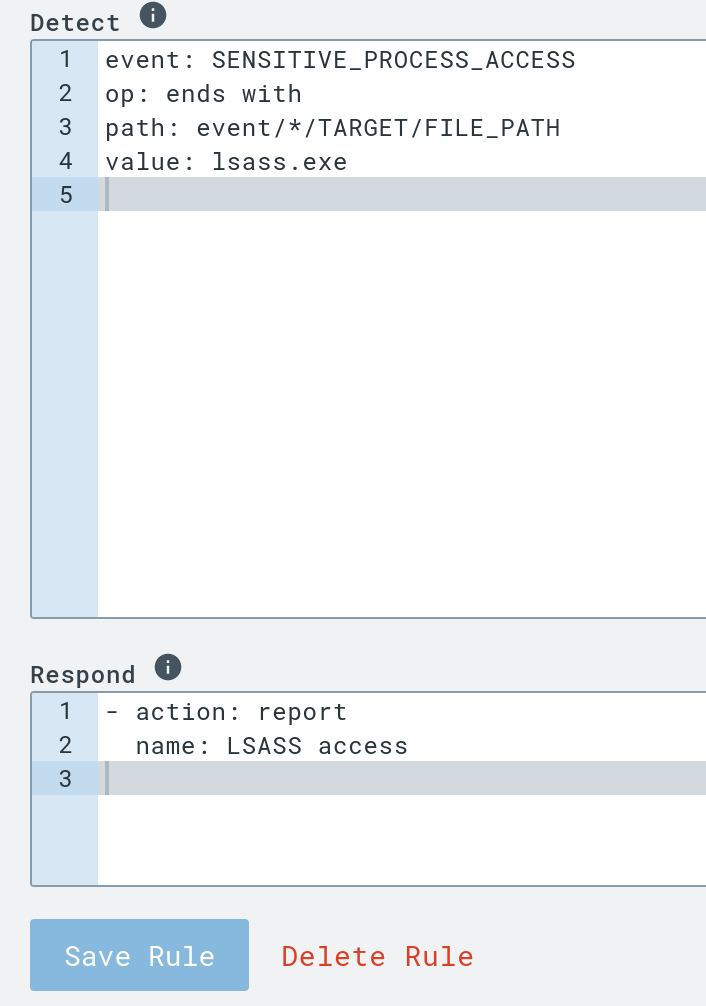
Now I know my basic rule works, which I can tell by seeing the “LSASS access” detection log after I ran the procdump again. This rule doesn’t block anything, so the next rule will focus on how to block a malicious command. The command is one which is a very likely indicator of a ransomware attack in progress.
vssadmin delete shadows /allFirst I ran this command through the C2 shell to execute it on the victim Windows VM.
An easy way to create a rule for an event is to click on the log that event generates and select the “Build D&R Rule” button. Then I made the rule to block the deletion of the Shadow Copies.
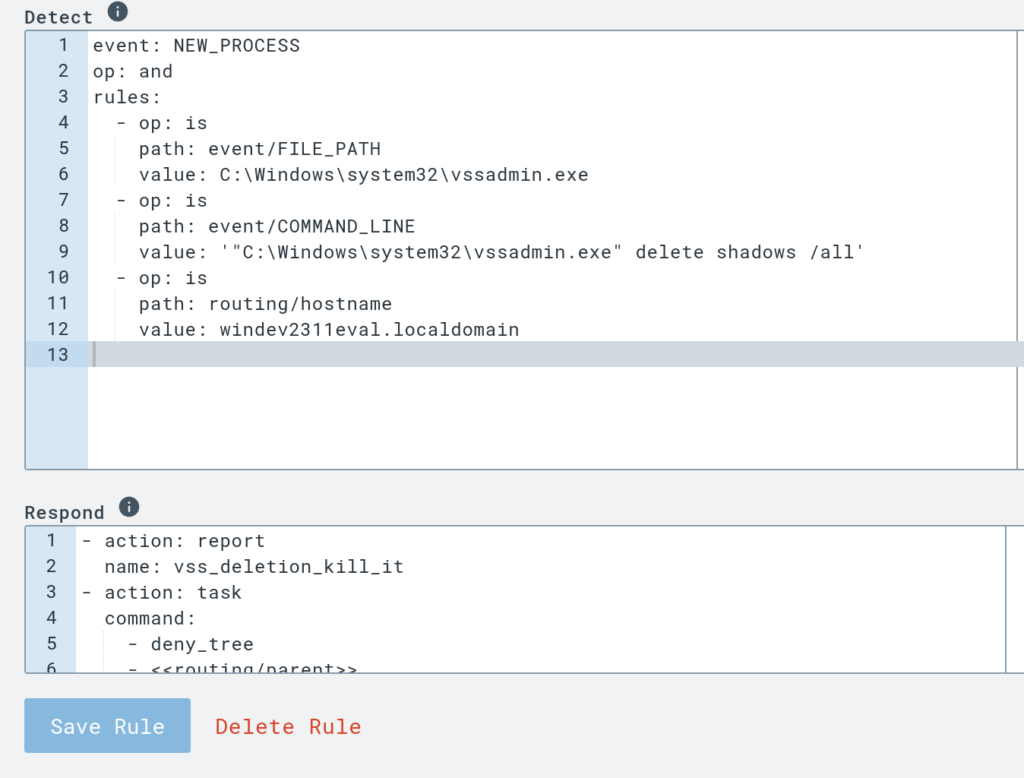
Now I will execute the command again and check the “Detections” logs to see if my rule worked.
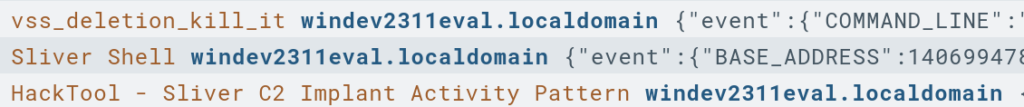
You can see that I was able to run the Sliver Shell (Sliver is the command and control server utility I used) but when I executed the command it was blocked by my new D&R rule.
Learning about False Positives
It’s common knowledge that false positives are very common for SOC analysts to encounter. It’s just difficult to have perfect rules which only trigger from genuine attacks. Part of this lab is learning what rules are more likely to cause false positives. Any process which is both normal to have running on a healthy system, but also has a potential to be involved in an attack is a huge source of false positives, especially if the rule is not well crafted. To simple of a rule will trigger everytime the process is running.
Another important piece of practical information I learned from my general research while preparing for a role in a SOC is how an IPS (Intrusion Prevention System) can cause problems much more than an IDS (Intrusion Detection System) when it comes to false positives. This wasn’t covered in depth in my studies for the Security+ certification. I was aware of the differences between an IPS and an IDS, but not the real world problems an IPS can cause. Because an IPS actual prevents instead of just detecting, a false positive can cause a reduction in availability of a system of network. I’m glad I learned this because my initial impression was that an IPS must be better because it actual stops the malicious process and I thought an IDS must have just been inferior since it can’t actually stop anything. After learning more about false positives, I can see why you may not always want to stop every thing which triggers an alert. There are certain processes which you would want to know are running so you can check if it’s running for a legitimate purpose without just automatically stopping it.
YARA Signatures
Another way to make sure you have D&R rules which fully encompass the scope of a potential attack is to look at the YARA signature. The YARA signature can offer additional commands which may accomplish the same attack. By making sure your rule blocks all the possible commands which may be used, you make the rule even more effective. An attacker may see one command is blocked by a rule and attempt to complete the attack by using different commands. It’s a very useful resource which I’m glad I know about now.
LimaCharlie can bring up various URL’s for resources to learn more about any given detection it logs. These URL’s can contain links to resources like the YARA signature for the detection. It really makes it easy to learn about the different detections it logs.
Automated YARA Scanning of Files an Processes
This project was my first exposure to dealing with YARA signatures. I had general awareness of how malware signatures are used in anti-virus/anti-malware programs, and some of their deficiencies, but I had never actually done anything with any sort of signature before. The scope of the CompTIA Security+ doesn’t really cover the different specific types of signatures in any depth. Learning about YARA signatures felt like digging into the details of how these theories I learned about for certifications are actually applied in a real world environment.
LimaCharlie has the ability to use YARA rules to perform scans, but you need to add a D&R rule to trigger an alert whenever a YARA detection occurs. The final part of this project is making and testing YARA rules in combination with the D&R rules to detect the Sliver C2 malicious payload, both as an .exe in the downloads folder, and as a process running in memory.

Summary
Overall, I found this lab to be a great way to get hands-on experience with tools that are useful for cyber security in general, but especially useful to prepare for a SOC environment. I am grateful to Eric Capuano for using his many years working in a SOC environment to help people like myself get an introduction to these useful skills. I’m also happy to get some unguided troubleshooting experience when problems popped up. I’m sure no matter how experienced and educated you are, there will always be unforeseen difficulties which require problem solving and a positive mentality.

0 Comments